Note: this feature is only available on enterprise plans. For more information, please reach out to our sales team.
We are very excited to announce a new feature for our enterprise customers: secrets management! Users can now easily create and manage sensitive information, such as API key or access tokens, and include them in their API monitors without exposing them in test results or 3rd-party integrations.
This feature request has been brought to us by a few customers, especially ones in highly regulated spaces such as finance, or healthcare, but we believe all of our enterprise customers will be able to benefit from it. Here at Runscope, we take extreme care with the security of our users' information, and we also like to provide tools for customers that will help them maintain any security standards they might have internally.
So, how does secrets management work?
Creating Secrets Variables
The team owner is the only person in a team who will be able to view the Secrets menu, as well as create/edit/delete secrets variables. After a secrets variable is created, any team member will then be able to use it in their API monitors.
If you're the team owner, click on the profile on the top-right and select Secrets from the drop-down:
In the secrets page, if you are the team owner you'll see Add Secret. Click on it to create a new secret key/value pair, enter the name that will be used to access it throughout your tests, and the value:
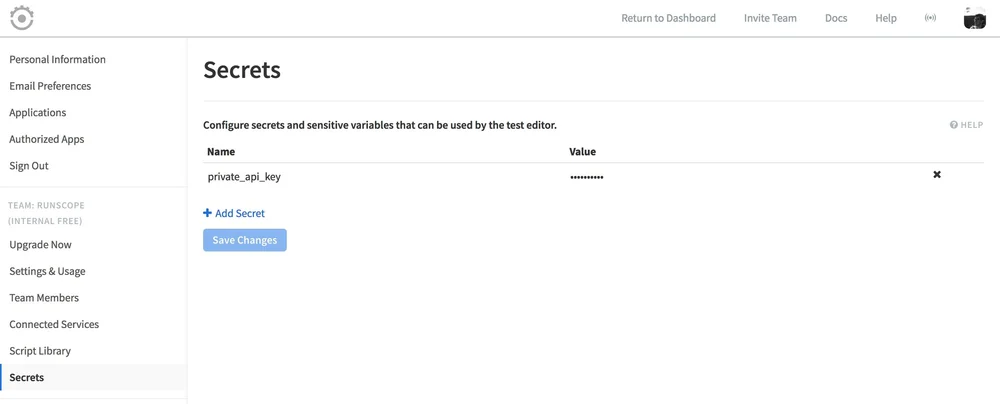
Click Save Changes, and you're all set!
Using Secrets
To use secrets in your tests, you'll have to use the built-in function get_secret(key_name), making sure to replace key_name with your secret's name:
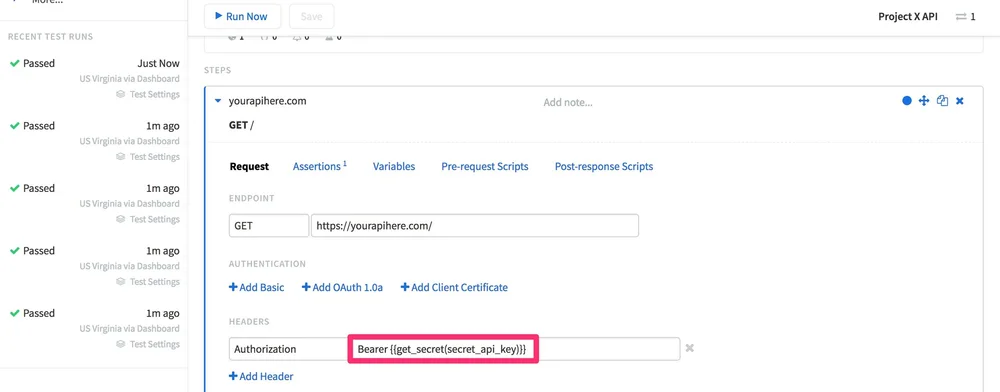
This built-in function can be used just like other Runscope built-in functions, which means you can add it to your environment settings, initial variables, pre-request/post-response scripts, etc.
Similar to how other built-in functions work, using it in Variables, Headers, or Endpoints will require you to format it with double-parenthesis like so: {{get_secret(key)}}.
For use in scripts, you can simply call the function without the parenthesis:
request.params.push({name:"api_key", value: get_secret("key")});
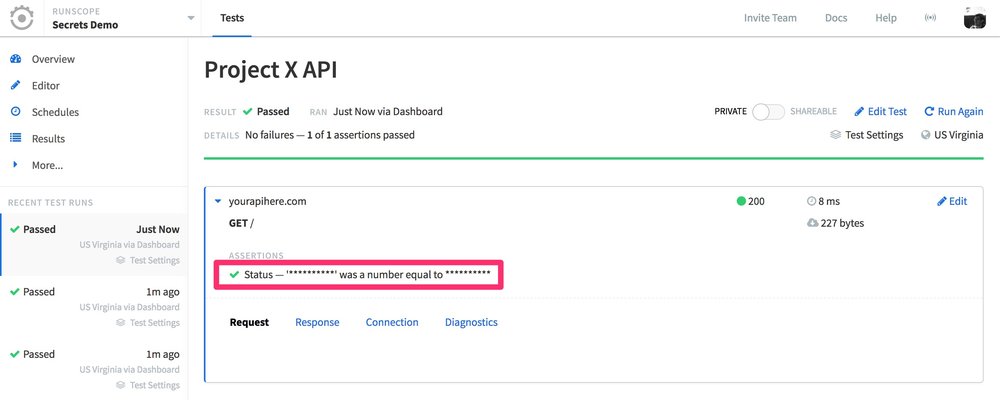
Whenever you have a step in your API tests that uses the get_secret function, in order to protect the secret, all assertions will be masked, and you won't be able to see any details in the Request tab, or the body for the Response tab:
For the latest information and details on the feature, please check out our Secrets Management docs. And if you have any questions or feedback, please let us know!